The iboss Zero Trust Secure Access Service Edge includes an asset catalog that inventories laptops, desktops, servers, IoT, OT and other devices that interact with sensitive resources. Cataloging assets is critical to for a robust cybersecurity strategy and ensures assets remain healthy, compliant and secure before accessing sensitive applications and data. The asset database provides a view of the assets across the organization and their current state to ensure devices that are lost, stolen, infected or compromised can easily be identified and the issue remediated.
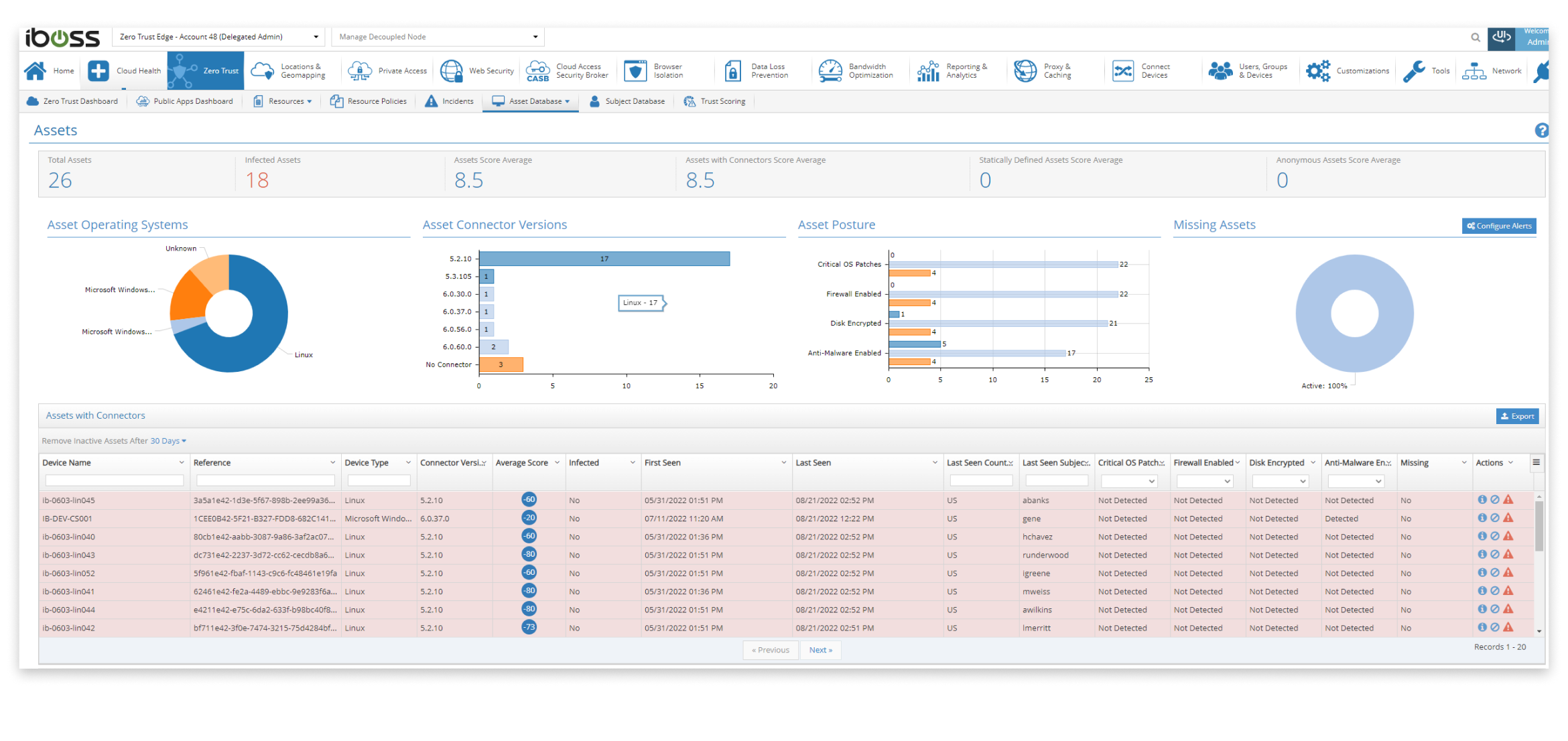
Asset database captures all devices interacting with sensitive applications and data
The asset database automatically adds devices connected through the iboss Zero Trust Secure Access Service Edge that are accessing sensitive applications and data. This includes enterprise-owned assets as well as other devices that are granted access to sensitive resources. This provides an inventory of all assets throughout the enterprise that are being managed and need to meet minimum standards to access enterprise resources. Statistics are provided to show which assets have critical patches installed, have their firewall enabled, have their disk encrypted and have anti-malware running. The list can also be exported through the console or via API.
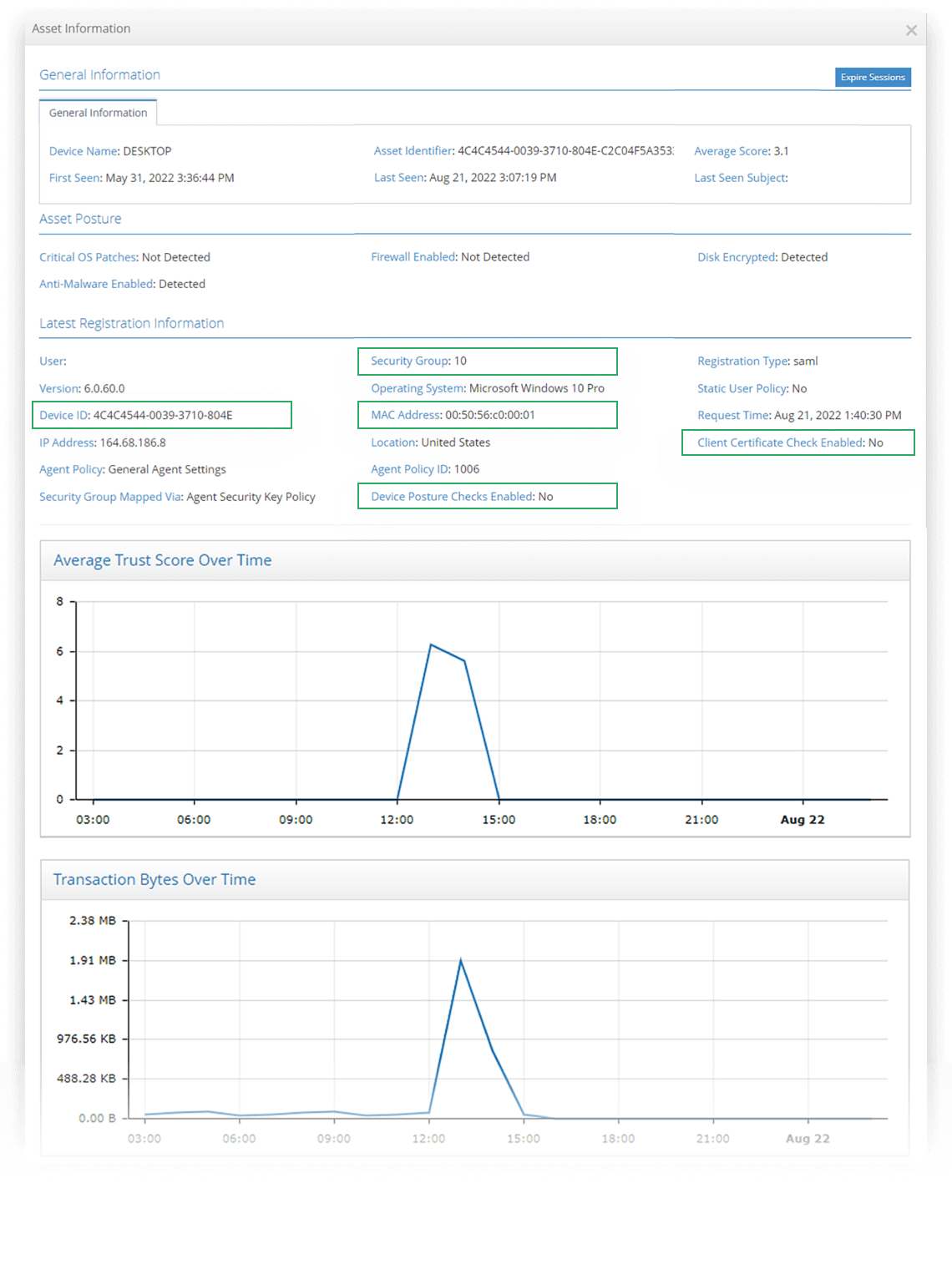
Asset details include Mac Address, device name, asset posture state and patch levels
Directly from the iboss single pane of glass admin console, access to asset details are easily obtained from the asset catalog. Details include the asset Mac Address, Device Name, last time the asset was seen as well as critical asset posture check statuses for critical OS patches, firewalls, disk encryption and antimalware. Details also include the device geo-location. The iboss Zero Trust Secure Access Service Edge also has visibility into every single transaction between the asset and protected resources and uses this to provide details into which resources the asset has touched as well as which users have logged into the asset. This can be used to reduce risk or determine impact level if an asset were to become compromised by providing an understanding of which applications, service and users the asset has interacted with.
Automatically terminate access to all resources for any asset when lost, stolen or infected
The iboss Zero Trust Secure Access Service Edge can terminate access to all resources for any asset. This is because the asset can only access those resources through the iboss Security Service Edge.
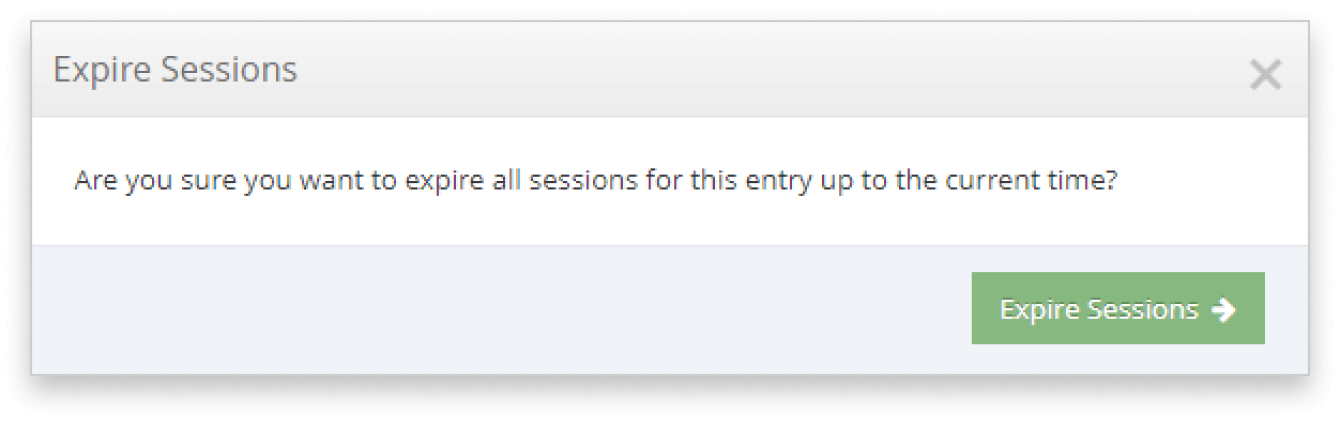
If a device is lost, stolen, compromised or becomes infected with ransomware, access to all applications, services and data can be terminated directly from the admin console. And because the iboss platform is 100% API accessible, Security Operations Centers can cut access with workflows, playbooks or via SOAR platforms. This simplifies and speeds response times for security incidents.
Realtime and historical asset risk score identifies risky systems
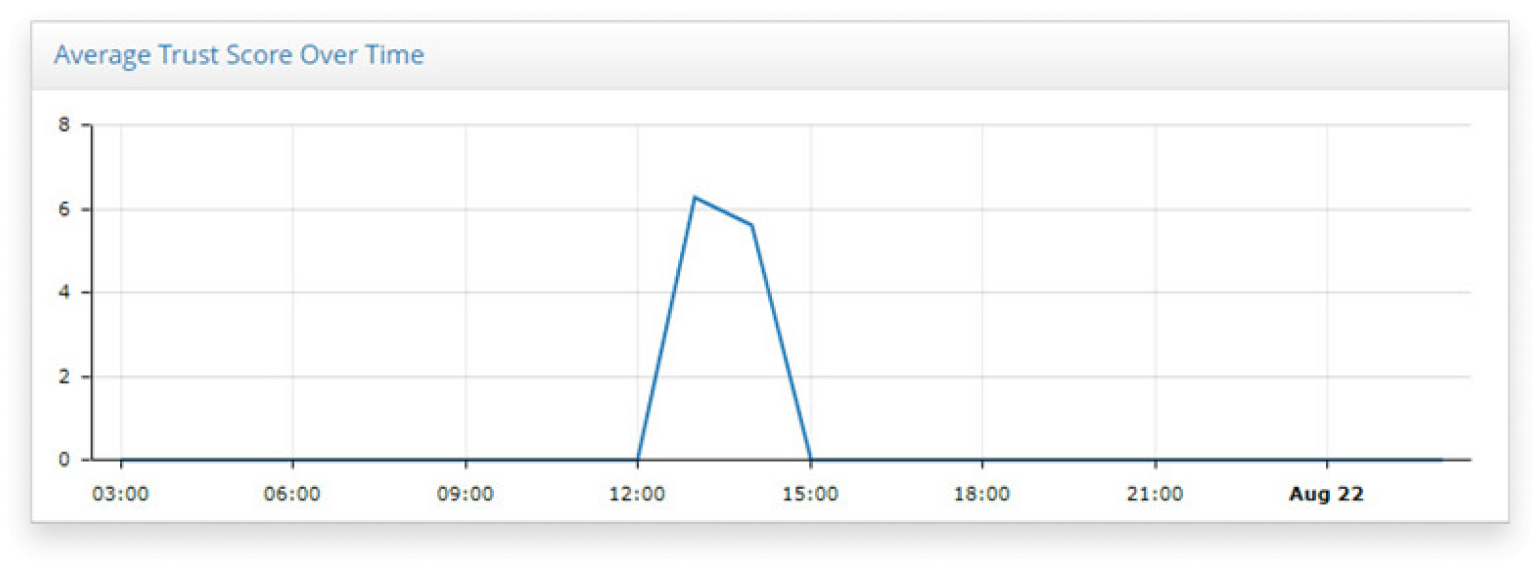
The iboss Zero Trust Secure Access Service Edge continuously scores assets as they interact with resources within the enterprise and throughout the cloud. Every transaction produces a real-time score that indicates risk level for that asset.
The score is continuously evaluated to capture the asset score at any moment in time. The score is also captured and logged historically to see how it changes over time. Drops in score can indicate higher risk, such as a critical patch not being installed on the asset.
This allows risk to be reduced substantially by ensuring action is proactively taken as an assets score changes over time.
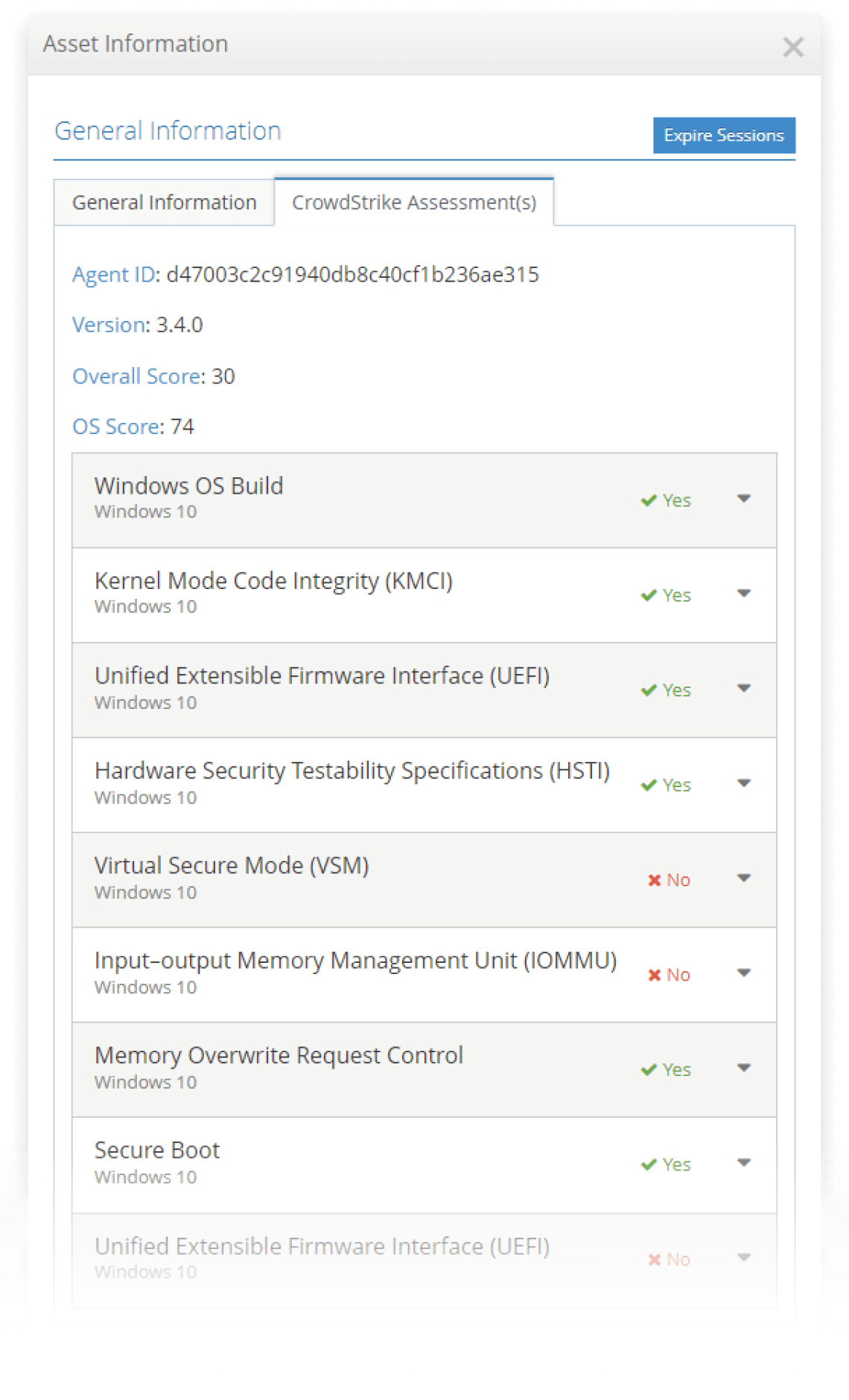
Includes Crowdstrike Zero Trust posture details
The iboss Zero Trust Secure Access Service Edge continuously scores assets as they interact with resources within the enterprise and throughout the cloud. Every transaction produces a real-time score that indicates risk level for that asset. The score is continuously evaluated to capture the asset score at any moment in time. The score is also captured and logged historically to see how it changes over time. Drops in score can indicate higher risk, such as a critical patch not being installed on the asset. This allows risk to be reduced substantially by ensuring action is proactively taken as an assets score changes over time.