Download Solution Brief DOWNLOAD PDF
The iboss Zero Trust SASE offers Browser Isolation to safely provide access to cataloged resources for users on personal or non-organization owned devices. This capability ensures that sensitive data remains within the resource and doesn’t reach the end-user device, significantly reducing potential data loss risks. Browser Isolation can now be configured directly from the Zero Trust Resource Database within each cataloged resource.
The challenge of accessing sensitive resources from non-organization-owned devices is the potential risk of data leakage. The iboss Zero Trust SASE recognizes this concern and addresses it adeptly with the Browser Isolation feature. With the platform’s resource catalog, organizations can identify and constantly adapt access to sensitive resources. When users access from organization-owned devices, data remains within a controlled environment. However, when guests or contractors, using personal devices, require access, the data poses a risk. Browser Isolation emerges as the solution, enabling these users to interact with the resources through a pane-of-glass, akin to a VDI interface. As a result, data stays confined to the resource, never venturing onto unsecured devices. With iboss’s capability, any resource within the Zero Trust Resource database can be optimized for access from unmanaged devices. Coupled with tailored configuration options and SAML authentication requirements, it delivers a blend of accessibility and security.
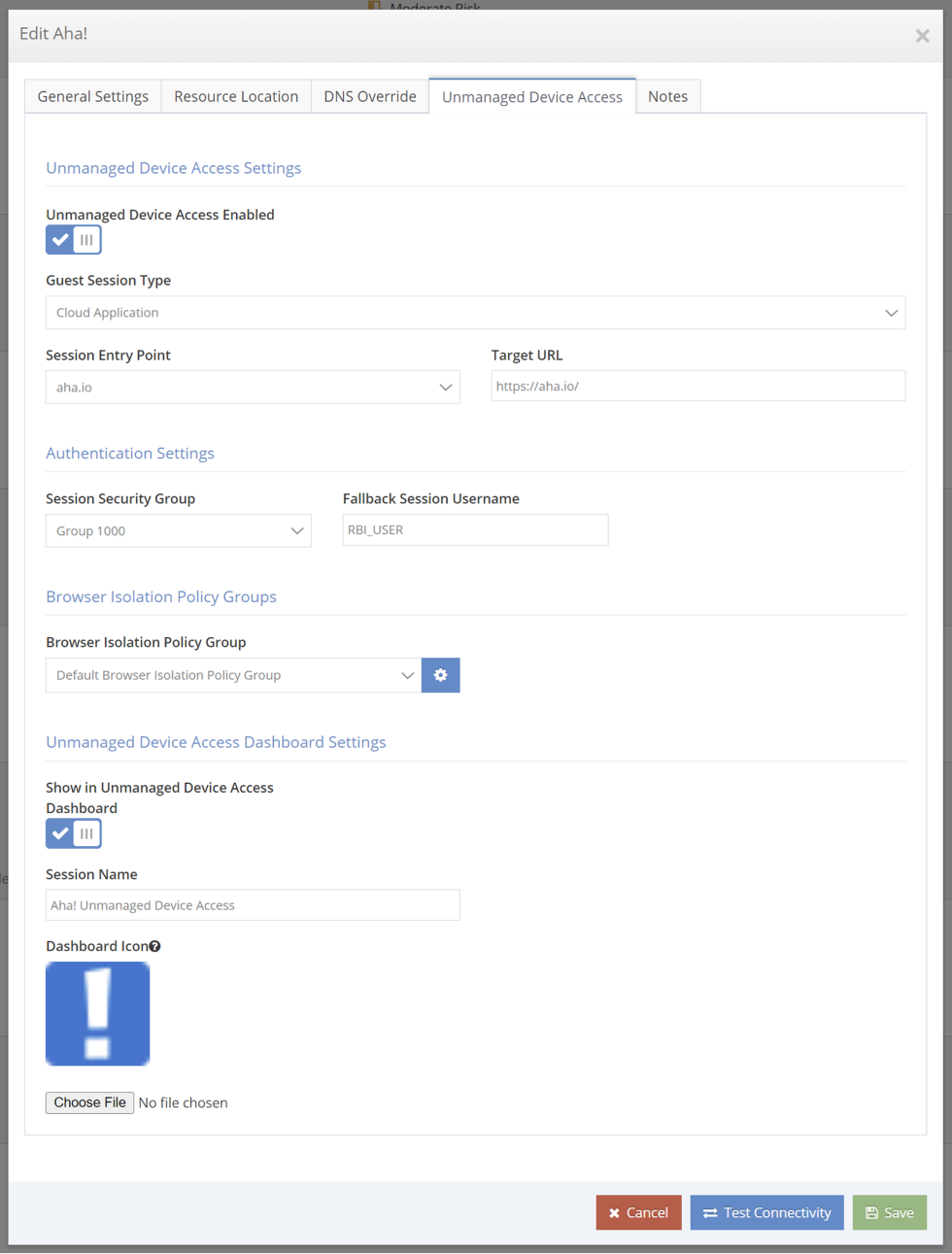
This capability extends and simplifies Browser Isolation configuration by allowing Browser Isolation access to be directly configured within each resource that is cataloged within the Zero Trust Resource Database. This provides clear visibility of which resources have been configured for unmanaged device access.
Benefits
- Resource Cataloging: The iboss platform allows cataloging of sensitive resources for adaptive access decisions.
- Data Security: Ensures data remains within the resource, preventing potential leaks on unmanaged devices.
- Controlled Access: Data accessed on organization-owned devices stays in a controlled environment.
- Custom Configurations: Resources in the Zero Trust database can be tailored for unmanaged device access.
- Pane-of-Glass Interaction: For unmanaged devices, users access resources through a secure pane-of-glass.
- Application Dashboard: Users can view all assigned resources configured for unmanaged device access after authentication.
How it Works
- Catalog Resources: Resources are cataloged within the Zero Trust Resource Database.
- Configure Resource Policies: Resource Polices for cataloged resources are configured to define access and authentication requirements for managed device access.
- Configure Resources for Unmanaged Device Access: Edit resources that require access from unmanaged devices and configure Browser Isolation options within the Unmanaged Access tab of the Resource modal.
- Enable App Dashboard: Configure resources so that they appear in the App Dashboard for easy access from unmanaged devices.
- Configure Modern Auth: Resources can be configured to require SAML authentication
Contact Us
Contact Us
If you’d like to speak to a sales representative, please take a moment to complete the form and an iboss representative will contact you shortly.
To speak with an iboss representative now, please call:
North America:
+1-877-742-6832 ext. 1
UK & Ireland:
Non UK International:
+1-858-568-7051 ext. 1
LATAM:
+1- 877-742-6832 ext. 7424