- Replace Legacy VPN
• The iboss service runs transparently and automatically allowing users to connect to on-prem resources without ever turning on a VPN again - Offload Traffic to the Datacenter
• Increase speeds, increase productivity and reduce costs by allowing users to connect directly to SaaS apps with security & logging in place - Continuous Adaptive Access Policies
• Evaluate every request to on-prem, SaaS and Cloud resources and immediately terminate access when something goes wrong, such as a device becoming infected - Step Up Authentication
• Ensures Federated Identity & MFA can be forced across all enterprise-owned resources - SSO & MFA for Legacy Apps
• Ensures modern authentication & MFA is performed even when apps do not support it - Supports Device Posture Checks
• Ensure Antimalware is running, firewall is on & and disk is encrypted on devices for security & sompliance - Automatic Resource Discovery & Classification
• Automatically discover shadow IT and understand what services exist that need to be protected - Built-in Resource Catalog
• The iboss service enables classification and a catalog of protected apps and services - Asset & Device Catalog
• The iboss service catalogs assets and devices that ensure devices are healthy, compliant & secure - Resource Labeling by Type & Security Objective
• All resource applications, data, and services can be classified and categorized to enable risk assessments
Key Benefits to Upgrade to iboss Zero Trust
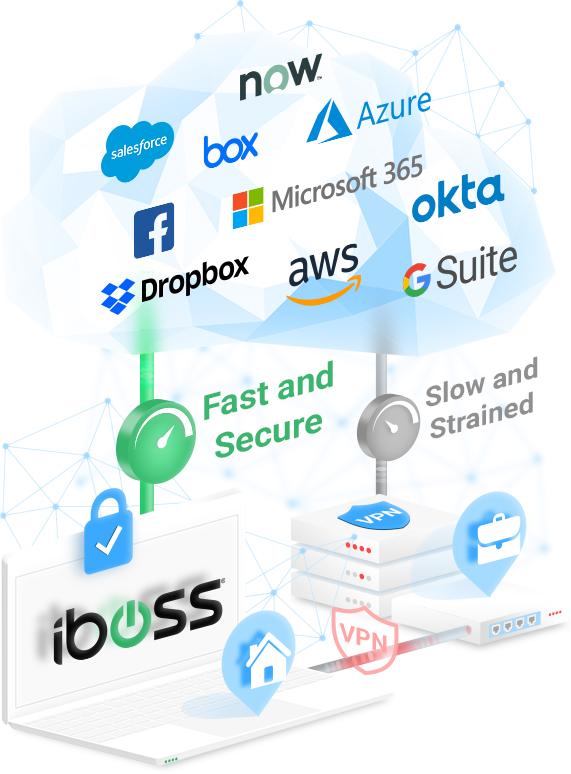
The shift to a zero trust allows organizations a Private Access VPN Replacement and ensures fast compliant and secure connections from any location
Cloud application traffic from remote users is traditionally sent through slow and overloaded VPNs to provide network security for compliance, malware defense and data loss. This typically results in slow connections or down networks preventing users from working effectively in work from home scenarios. The problem is, cloud application traffic should NOT be sent through VPNs. If the traffic is destined to the cloud, why is it being sent back to the office?
The iboss Zero Trust Secure Access Service Edge can completely offload your VPN connections by sending cloud application traffic directly from work from home users to the cloud. All of the traffic is sent through the Platform first, to ensure compliance, malware defense and data loss prevention. This immediately reduces or eliminates load from VPN connections bringing the network back up to normal operation and ensuring users are productive while working from home.
Continuous Adaptive Access Policies Provide Conditional Access to Resources
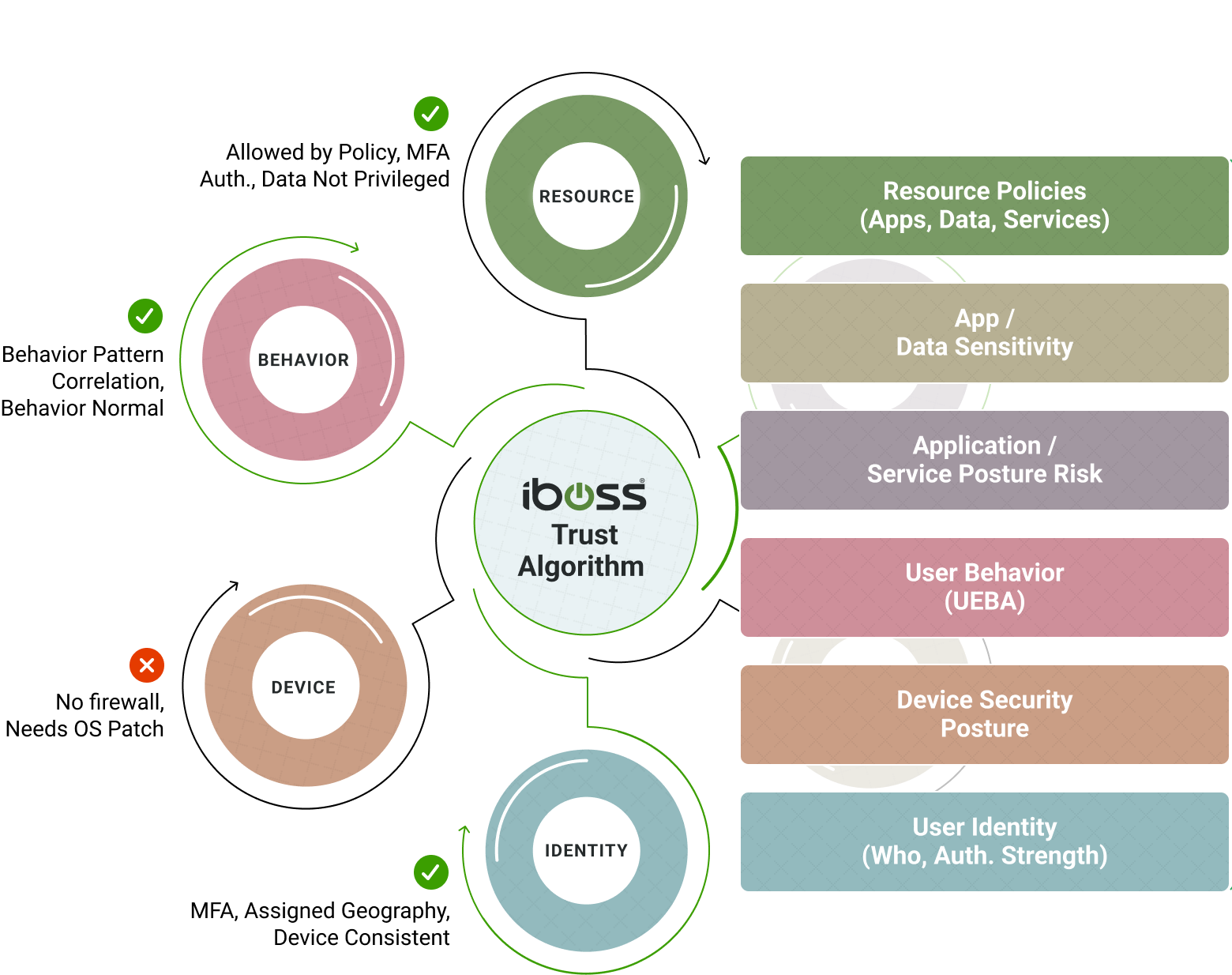
The NIST SP 800-207 Zero Trust Architecture defines a framework for adaptive access trust algorithms which includes receiving a series of signals from various sources, running them through a trust algorithm within the Zero Trust service, and making a final decision of whether to authorize access or deny access to a protected resource. This is an important design concept as the signals that are analyzed include user signals, such as how the user is authenticated, device signals, such as whether the device is infected, and others that are available at the time access is needed to a resource. The trust algorithm ingests all signal types in a unified method and uses them to make a final determination for access. The iboss Zero Trust Secure Access Service Edge follows this design pattern by combining the various signals and analyzing them via the configurable trust algorithm to take actions. Actions include denying access to a resource – for example, when a device is infected, isolating access to a resource, increasing the trust score or decreasing the trust score for the transaction.
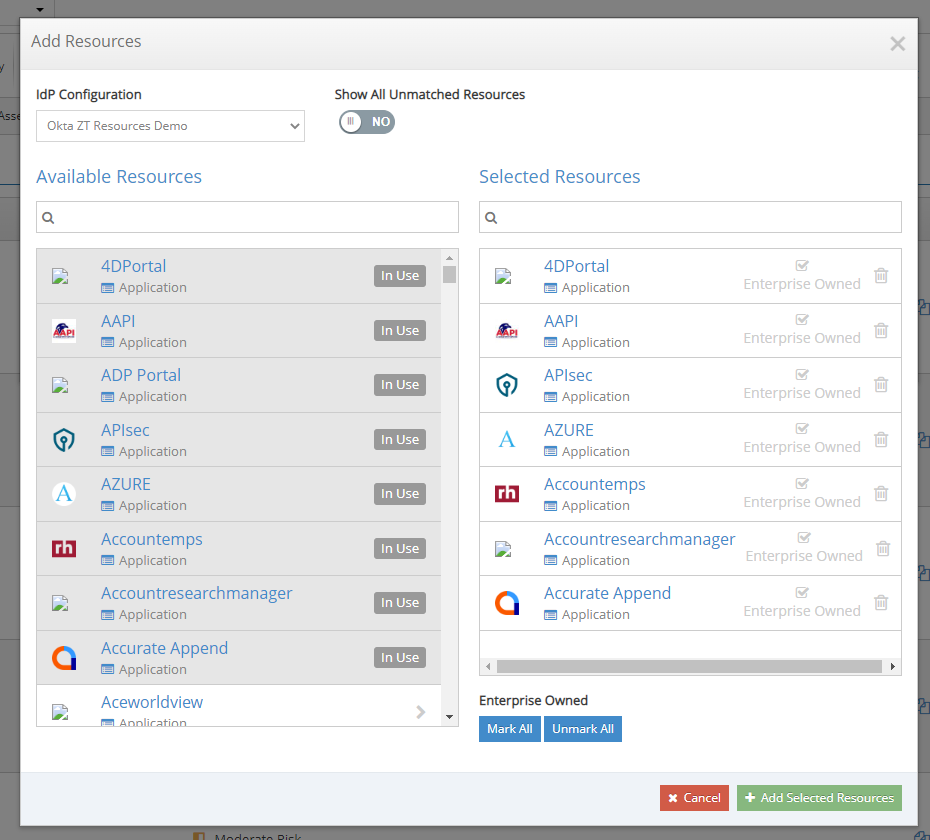
Built-in Resource Catalog Enables Classification of Protected Apps and Services
The iboss Zero Trust Secure Access Service Edge provides cataloging capabilities that can be used to inventory what sensitive resources need to be protected. The resource catalog organizes applications and services which can be labeled by type and security impact. Understanding what resources exist within the enterprise is critical for understanding risk and creating appropriate access policies.
Zero Trust upgrade now available. Contact us now!

Upgrade your account to Zero Trust to take advantage of all these benefits. Reach out to your customer success engineer, email [email protected], or click Contact Us below.
