Purpose Built for Zero Trust to Protect Organizations from Breaches and Data Loss
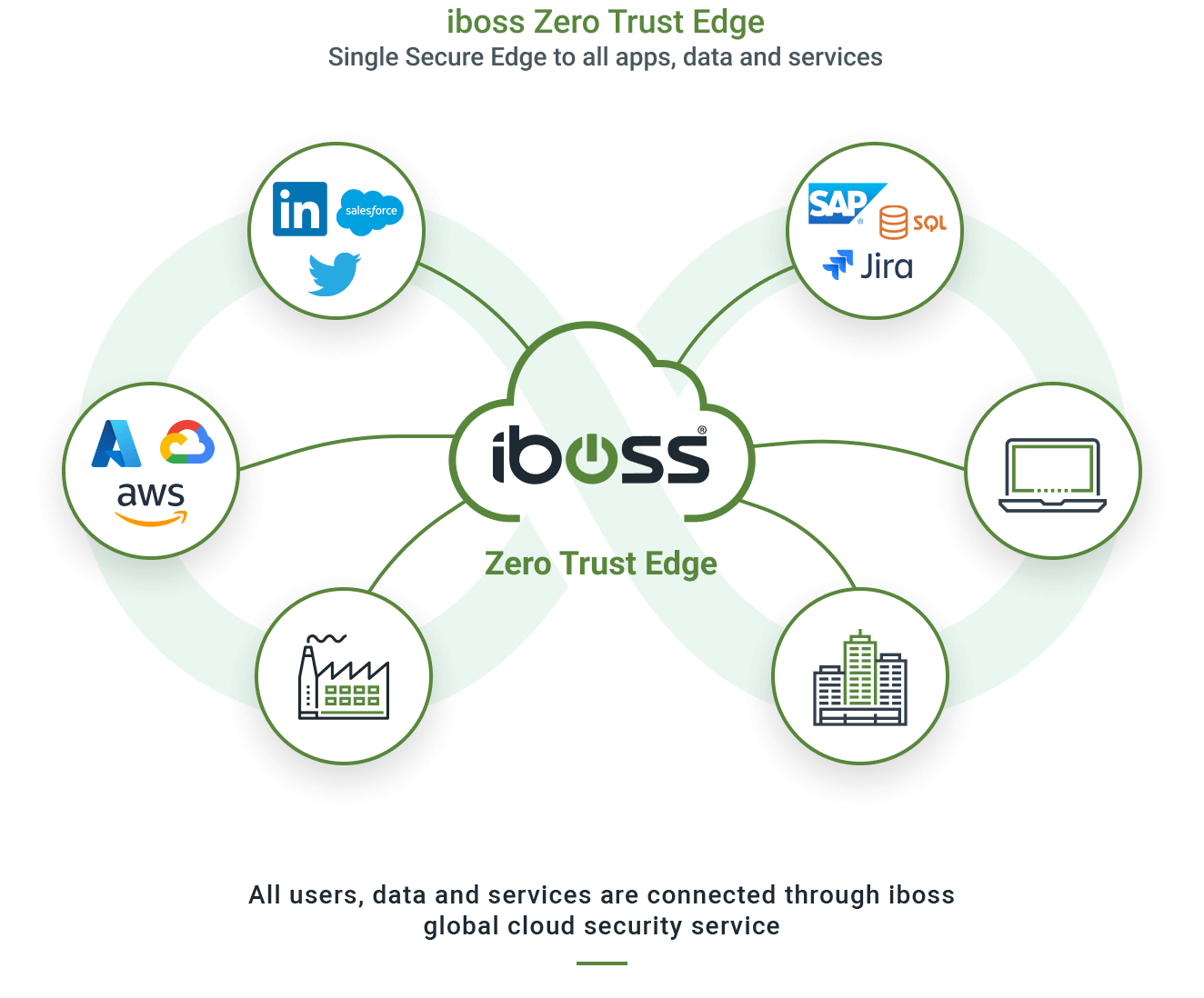
The iboss Zero Trust SASE prevents breaches by making applications, data and services inaccessible to attackers while allowing trusted users to securely and directly connect to protected resources from anywhere
Learn how the iboss Zero Trust SASE meets all requirements of NIST SP 800-207
Platform Overview
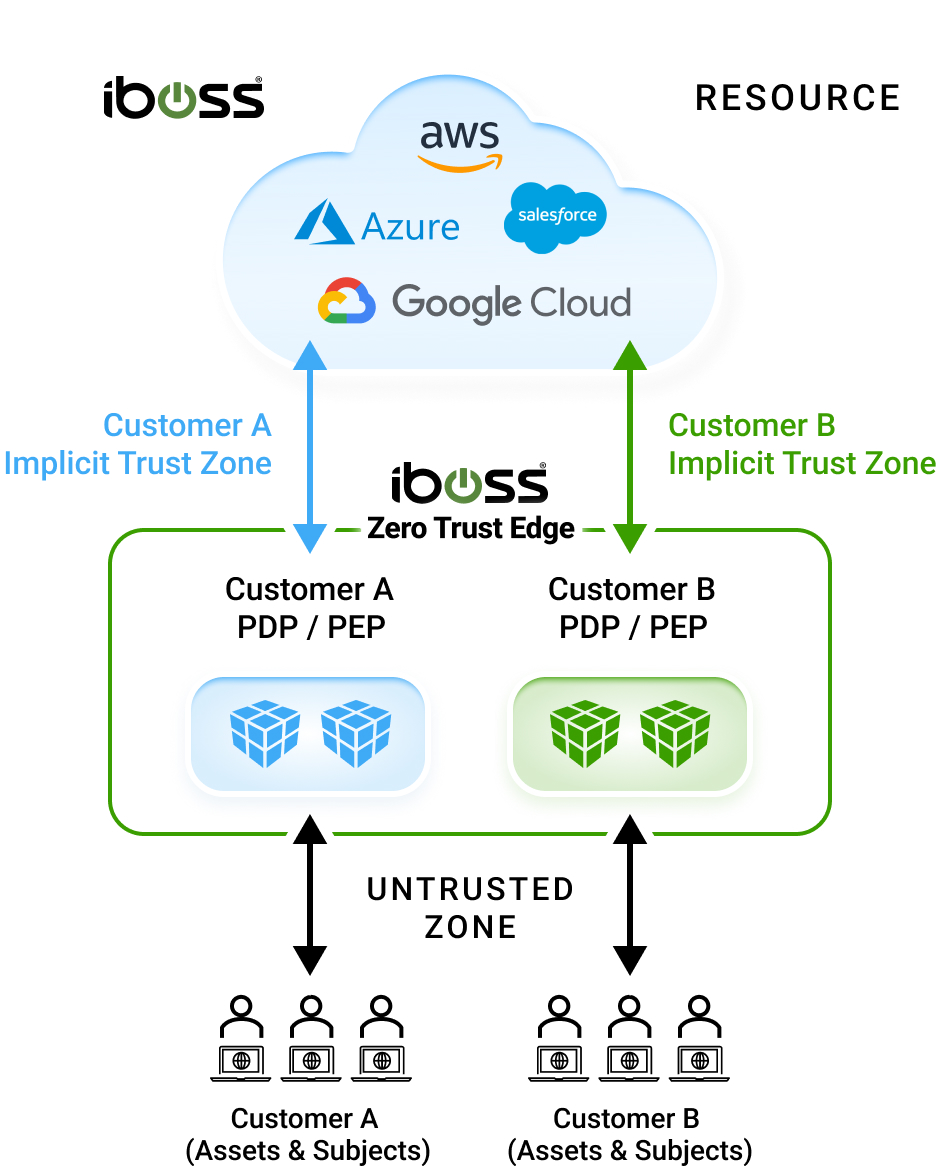
Applications, data and services have moved from the datacenter to the cloud, making them easily accessible by attackers. Users have left the office and are working from anywhere. Legacy security and visibility approaches rely on resources and users to be located in the office to provide protection which is no longer possible. The iboss Zero Trust SASE is focused on protecting sensitive resources by making them completely inaccessible and invisible to attackers while strictly granting access to trusted and approved users from wherever they work. With the surface area of protected applications, data and services reduced to zero and only accessible through the iboss Zero Trust SASE, cyber risk is greatly reduced, breaches and data loss are prevented and visibility and security are delivered consistently throughout the organization.
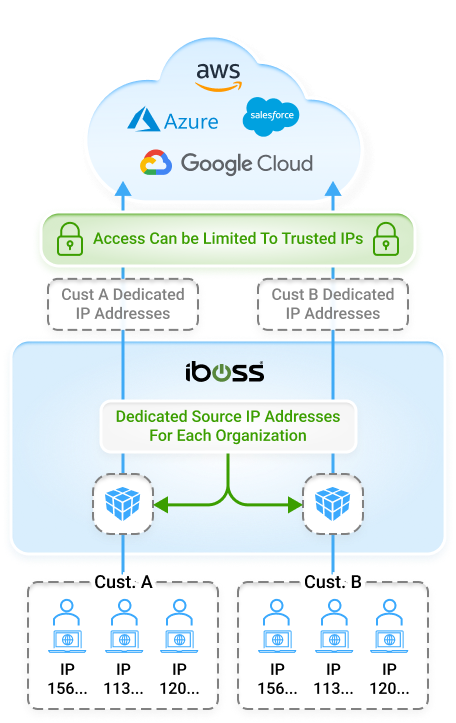
The iboss Zero Trust SASE allows all protected resources within an organization to be labeled and categorized, including Security Objectives and Impact Levels. This provides organizations with a clear understanding of where sensitive applications and data reside while providing insight into what users and assets are interacting with those protected resources. The iboss Zero Trust Service follows the NIST Risk Management Framework (RMF) and implements the NIST 800-207 Zero Trust Architecture Special Publication acting as the Policy Decision & Enforcement Point which is the heart of the NIST Zero Trust architecture model.
With all protected resources connected and only accessible via the iboss Zero Trust SASE, organizations can connect their users to the iboss cloud which dynamically provides direct access to applications and data without ever needing to turn on a VPN. The protected resources can reside on-prem or in the cloud. The iboss Zero Trust SASE service handles connecting only the approved and trusted users to the resources automatically. This improves end-user experience and dramatically increases productivity as users get ultra-fast connections from any location.
The iboss Zero Trust SASE goes beyond authentication and instead inspects and authorizes every single transaction between a user and protected resource, using authentication as one of many signals to allow or deny access to protected resources. This ensures every transaction is inspected for CASB, malware defense and data loss prevention to eliminate the shadow risk that typically exists between authentication and sensitive data access. The iboss Zero Trust SASE continuously evaluates, protects and logs every access to every protected resource, preventing breaches and data loss.
NIST Risk Management Framework Applied To Zero Trust
Designed To Manage Risk Centered Around Effectiveness & Efficiencies
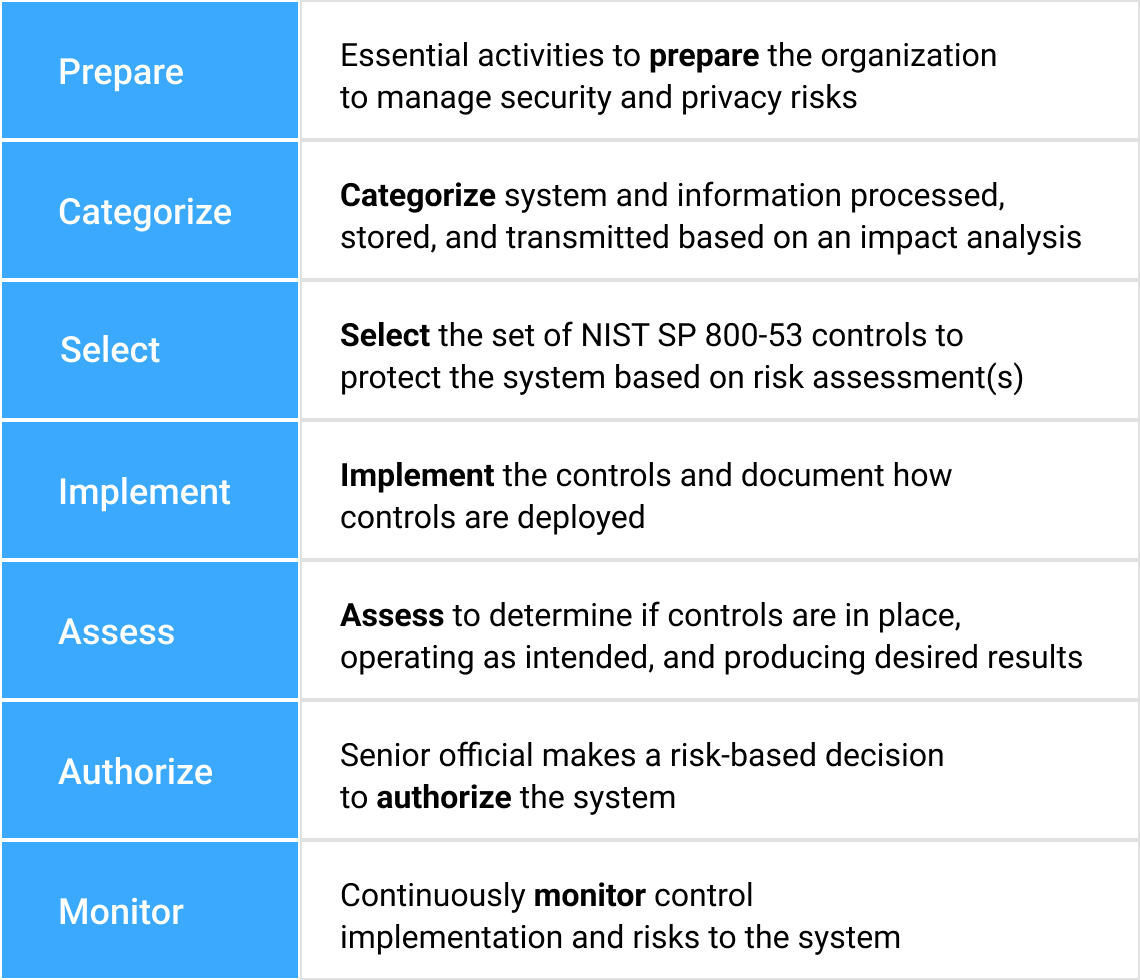
Greatly reducing cyber risk resulting in breaches and data loss is easily made possible using the iboss Zero Trust SASE because it tackles the problem from the various angles that make organizations vulnerable to attacks. The platform provides the tools to follow processes outlined in the NIST Risk Management Framework which starts by understanding and classifying what resources exist and need to be protected. Resources are any application, data or service that an enterprise owns and wants to protect from breach which can exist on-prem or in the cloud. The sensitive resources are then connected to the iboss Zero Trust SASE. Next, users and assets that need access to connected sensitive resources are pushed through the iboss Zero Trust SASE for access. This allows for security and visibility as the users and assets interact with the protected resources. Once all users are connected to the iboss Zero Trust SASE, the resources are locked to the iboss Zero Trust SASE so that they are completely invisible and inaccessible directly and can only be accessed through the iboss Zero Trust SASE. Cyber risk is reduced as each resource is connected to the iboss Zero Trust SASE and ultimately a complete Zero Trust transformation occurs when all resources have been protected by the service. Users also gain the benefit of eliminating the need to turn on VPNs to access resources as they are always connected to resources from wherever they work.

NIST Risk Management Framework
This definition focuses on the crux of the issue, which is the goal to prevent unauthorized access to data and services coupled with making the access control enforcement as granular as possible. That is, authorized and approved subjects … can access the data to the exclusion of all other subjects (i.e., attackers).
– Page 4, NIST SP 800-207
NIST Zero Trust Architecture (SP 800-207)
- NIST SP 800-207 provides a detailed definition of Zero Trust that can be implemented by technology (i.e. iboss)
- NIST Zero Trust is centered and anchored around the resources an organization is actively trying to protect
- Resources are any resource the organization wishes to protect (including applications, data and services, IoT, etc.)
- Includes resources at any location – cloud resources and on-site resources
- An organization must understand and categorize those resources
iboss Implementation of
NIST SP 800-207 Zero Trust Architecture
Resources Cannot Be Accessed Without Going Through The Policy Enforcement Point And Gaining Authorization
NIST SP 800-207 Zero Trust Framework
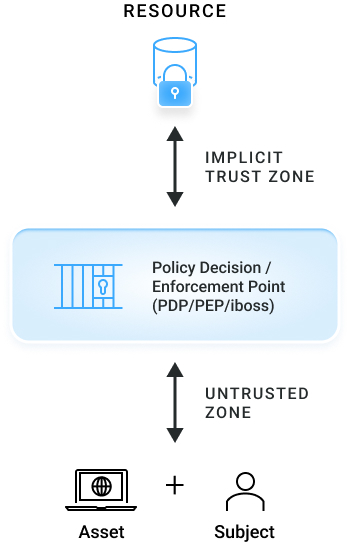
iboss Implementation Of NIST SP 800-207
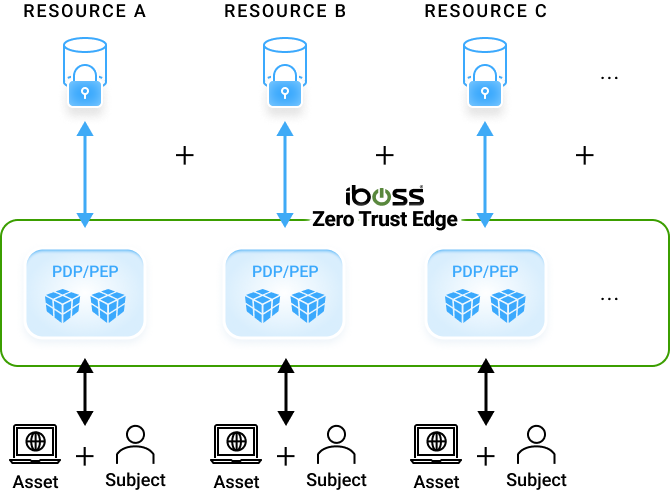
Key Definitions
Resource
Data, application, or service being protected, can be on-prem or in the cloud
“Policy Enforcement Point” (PEP) /
“Policy Decision Point” (PDP)
A binary “checkpoint” which either grants or denies the subject/asset access to the resource – iboss Zero Trust Service
Asset
Laptop – or IoT device, etc.
Subject
User – although a subject can be non-human (e.g. an API service)
A Guide To Implementing Zero Trust With iboss Zero Trust Platform
Categorize and Classify Protected Applications, Data and Services
The first step is to classify the applications, data and services that are owned by the enterprise and need to be protected. The iboss Zero Trust SASE provides the ability to create an inventory of all resources used within an enterprise which is a critical first step to understanding and reducing risk. In addition, iboss provides the capabilities to tag resources with labels which are used to classify the resources by type. This creates an inventory of what needs to be protected to reduce risk for an organization.
By labeling each sensitive resource, an organization can then understand the impacts to the organization should a breach occur. This sets a major milestone for risk reduction as most organizations do not have the tools and have not gone through the process of understanding their sensitive application, data and service landscape.
Identification & Classification Of All Company Resources And Their Associated Impact Levels
1. Identify All Resources Within An Organization
Identify all resources that are input, stored, processed and/or output from each system – a resource is any data, application, or service either on-prem or in the cloud that needs to be protected
2. Tag All Resources With A Resource Type Label
iboss facilitates resource identification and grouping with smart labels, which tie a particular resource to a Resource Type (e.g. HR System, CRM System, Code Repository System)
3. Determine Potential Impact Level Of Resource Type
For each identified Resource Type, determine the potential impact level if the Security Objective is compromised. This critical step determines where risk lies within the organization.
Assign Security Objectives and Security Impact Levels to Resources
iboss smart labels allow for Impact Levels assigned to each Resource Type to be automatically applied to every associated resource


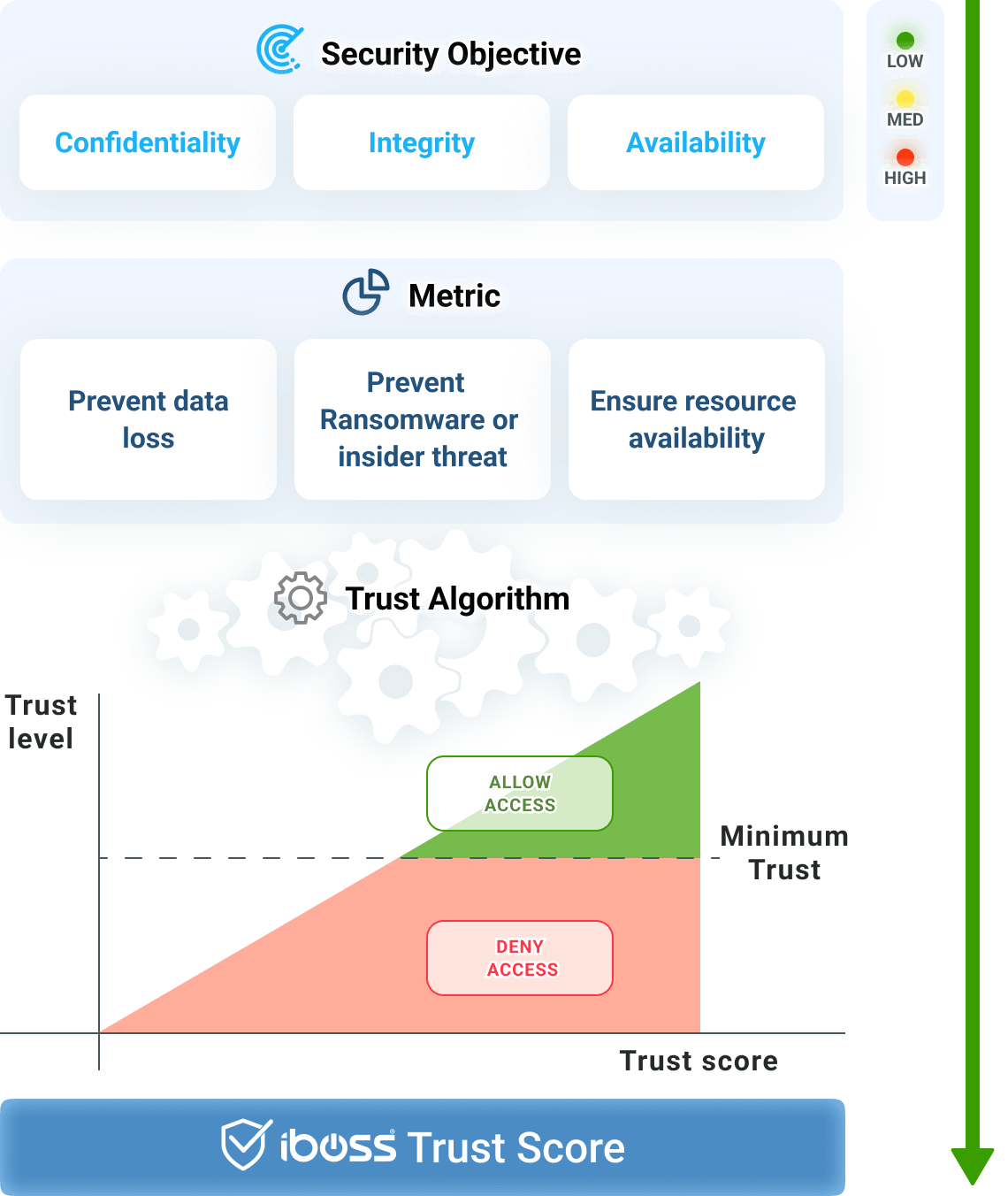
Once resources are labeled, they can then be assigned security objective impact levels. The iboss Zero Trust SASE focuses on three Security Objectives as defined by FIPS199:
- Confidentiality – Preventing Data Loss
- Integrity – Preventing the destruction of information (Preventing ransomware or insider threat)
- Availability – Ensuring that critical resources are available to the organization
For each of the three security objectives above, the platform allows a Security Impact Level to be assigned:
- Low – Limited adverse effects on the organization
- Moderate – Severe adverse effects on the organization
- High – Catastrophic adverse effects on the organization
Once each resource is associated with security impact levels, the iboss Zero Trust SASE will track and log interactions between users, assets and the resource to provide clear and continuous visibility into organizational risk. Additionally, this provides the enterprise a clear understanding of what impact a resource has on organizational processes for continuity planning.
Connect Resources to the iboss Zero Trust SASE
Next, the resources are connected to the iboss Zero Trust SASE which ensures the Policy Enforcement Points within the global security edge can communicate with each resource directly. This includes connecting cloud and on-prem applications, data and services. The iboss Zero Trust SASE will become the “gate keeper” to these sensitive resources and make them completely private and inaccessible to attackers later.
Identified & Classified Resources Added To iboss Platform
4. Add All Company Resources To iboss Platform

Add all identified & classified resources to the iboss platform, enabling complete visibility into the traffic flowing to and from those resources

iboss cloud PDP/PEP initially set to allow all traffic, operating only in visibility mode
Subjects (users) seamlessly access company resources, while the iboss platform invisibly observes
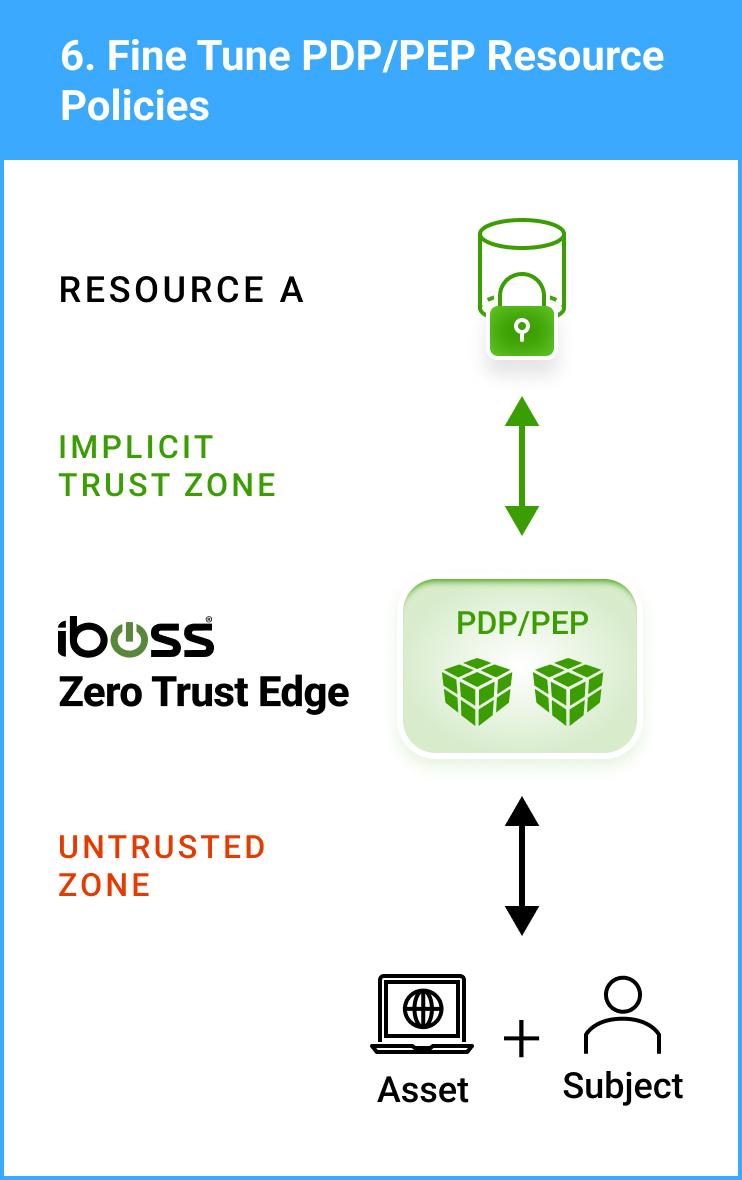
Assign Policies for Resource Access and Tune Trust Scoring Algorithm
The iboss platform follows the Zero Trust model, only approved subjects are allowed to access a protected resource while all others are denied. The platform allows Resource Policies to be created which define which users and assets should be granted access to a protected resource. Only those that meet the criteria will be considered when an access decision to a resource is being evaluated. In addition to the criteria-based policies, the iboss Zero Trust SASE allows for the creation of Trust Scoring Algorithms. Trust scores allow for adaptive security to dynamically grant or deny access based on the risk posture of the user, asset or resource. For example, if a trusted user should have access to a protected resource but they are using a laptop infected with ransomware, access will automatically be denied using the trust scoring algorithm.
Once policies are created for the resources, users are ready to be connected to the iboss Zero Trust SASE.
Connect Users
to the Zero Trust SSE
Connecting users through the iboss Zero Trust SASE ensures approved users will be able to access the resources they need to be productive from wherever they work. This eliminates the burden of having to turn on a VPN to access specific on-prem resources as the need for a VPN is completely eliminated. As long as they are connected to the iboss Zero Trust SASE, users will be connected to all resources they are approved to use automatically.
Lock the Protected Resource
to the Zero Trust SSE
Once all users are connected through the iboss Zero Trust SASE, the final step is to lock the protected resources to the iboss Zero Trust SASE so that the resources are only accessible through iboss. This makes the resources invisible and inaccessible unless explicitly granted through the iboss Zero Trust SASE, which becomes the gate keeper to all resources. The surface area for attack at this point is greatly reduced.
The goal is to get all users and assets connected through the iboss Zero Trust SASE which is protecting each resource.
Company Resources Only Accessible To Traffic From iboss PDP/PEP
5. Lock Down Access To All Company Resources
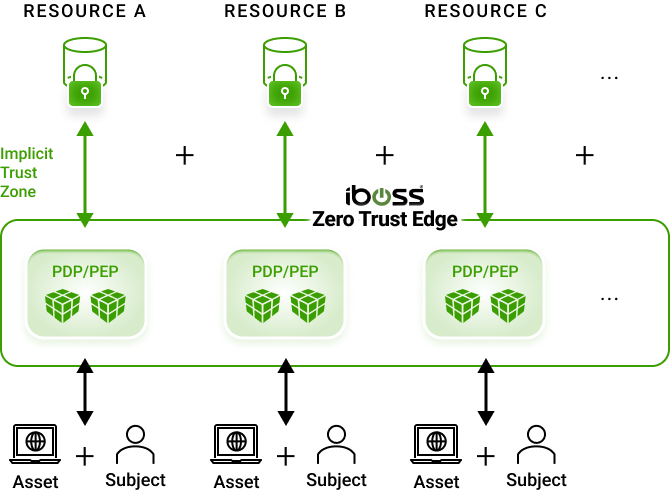

After all company resources have been added to the platform, organizations will have complete visibility and access control

iboss cloud resources set to allow only traffic from iboss PDP/PEPs, limiting access to only iboss inspected traffic
Authorized subjects (users) seamlessly access company resources, while the iboss platform protects and continues to observe
Gain Visibility Into Interactions Between Users, Assets and Protected Resources
With all transactions going through the iboss Zero Trust SASE, detailed risk reports are created which show how users, assets and resources are interacting. A continuous confidence score is generated for every user, asset and resource to understand overall organizational risk in real-time. The iboss Zero Trust SASE responds automatically to risky situations by requiring users to step-up authentication, for example by performing MFA, when accessing sensitive resources or the confidence level becomes too low. Reports can be generated to show how the organization’s security posture is improving over time with each and every step along the journey of a complete Zero Trust transformation.
Regardless of where the resource is located, security and visibility will always be consistently applied.
Confidence Level Algorithms Configured For Each Resource Policy To Allow For Real-Time Decision Making
Resource policies configured for each Resource Type factor in Security Objective and Impact Level to determine if subjects and assets have access to protected resources.
iboss resource policies encapsulate the decision-making process of the PDP/PEP to either allow or deny access based on the decision of the confidence algorithms
Criteria-based decision metrics and confidence level algorithms assign a confidence score in real-time to primary actors in the zero-trust framework: Subject, Asset and Resource
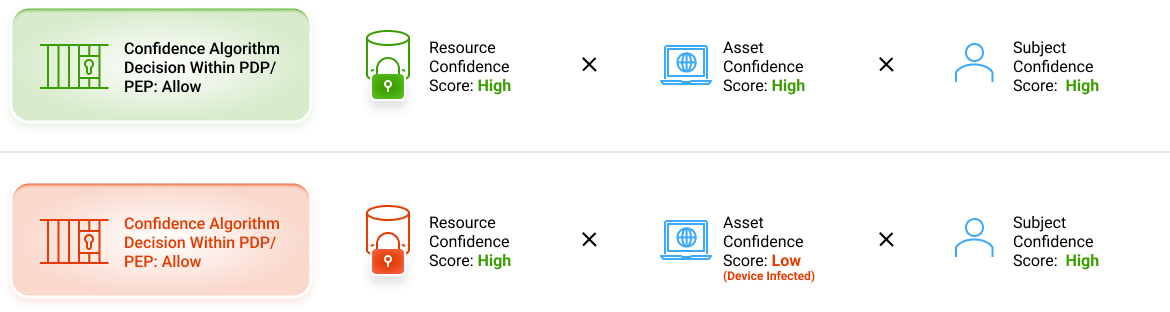
iboss confidence score is calculated at the time of transaction – when the risk occurs:
- For example, there is no risk for a user/hacker who has no access to resources at that time (e.g. in jail), an infected laptop that cannot access a resource (e.g. it is powered off), or a resource that is not connected.
- Risk occurs when all three (Asset, Subject and Resource) meet in an exchange
Greatly Reduce Cyber Risk from Breaches and Data Loss as All Sensitive Resources Are Now Private
With access to resources being made available only through the iboss Zero Trust SASE, an enterprise greatly reduces cyber risk and can prevent breaches and data loss. With resources spreading throughout the cloud and on-prem, the iboss Zero Trust SASE serves as the interface between users and assets that need access and the resources that need to be protected from breaches and data loss.