Having a clear picture what resources need to be protected within an enterprise is a critical first step creating a successful cybersecurity strategy to reducing risk. Understanding the landscape of applications, services and data provides the foundation for creating the Zero Trust policies that will protect them. When identifying and classifying sensitive resources, labeling allows them to be organized by type and security objective. This provides prioritization of the most critical resources to ensure those are addressed first and allows the organization to reduce catastrophic risk due to compromise of a mission critical application or service. The iboss Zero Trust Secure Access Service Edge provides the labeling and classification tools needed to identity and organize resources across the enterprise

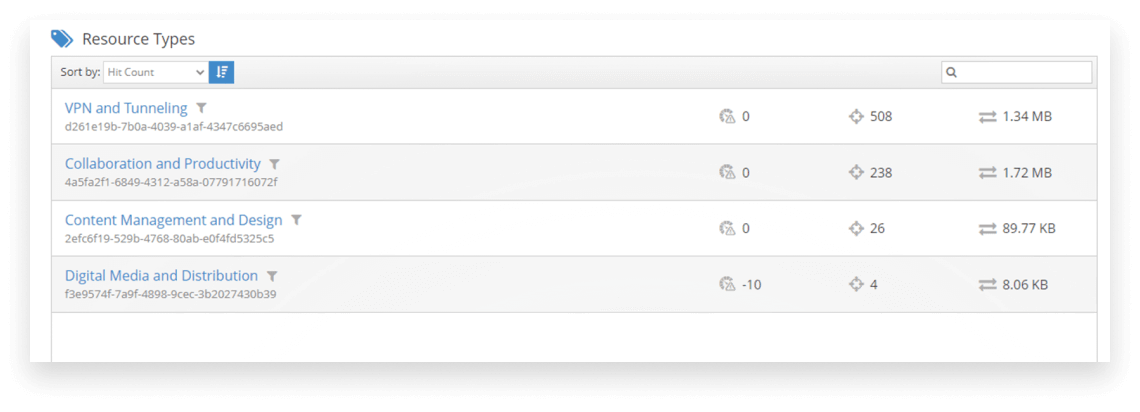
Resource tags allow resources to be organized by type and category
The iboss Zero Trust Secure Access Service Edge provides resource tags that are used to label resources and organize them by type and category. There are a large number of built-in resource tags and categories that can organize resources by department or functional area within an organization. Additionally, custom tags and categories can be created to ensure resources can be organized for any type of scenario or organization. Labeling resources with tags provides a central repository for all resources that is clearly organized and can be used for risk assessments or executive leadership presentations.

Classify resources by security objectives and impact levels according to FIPS 199
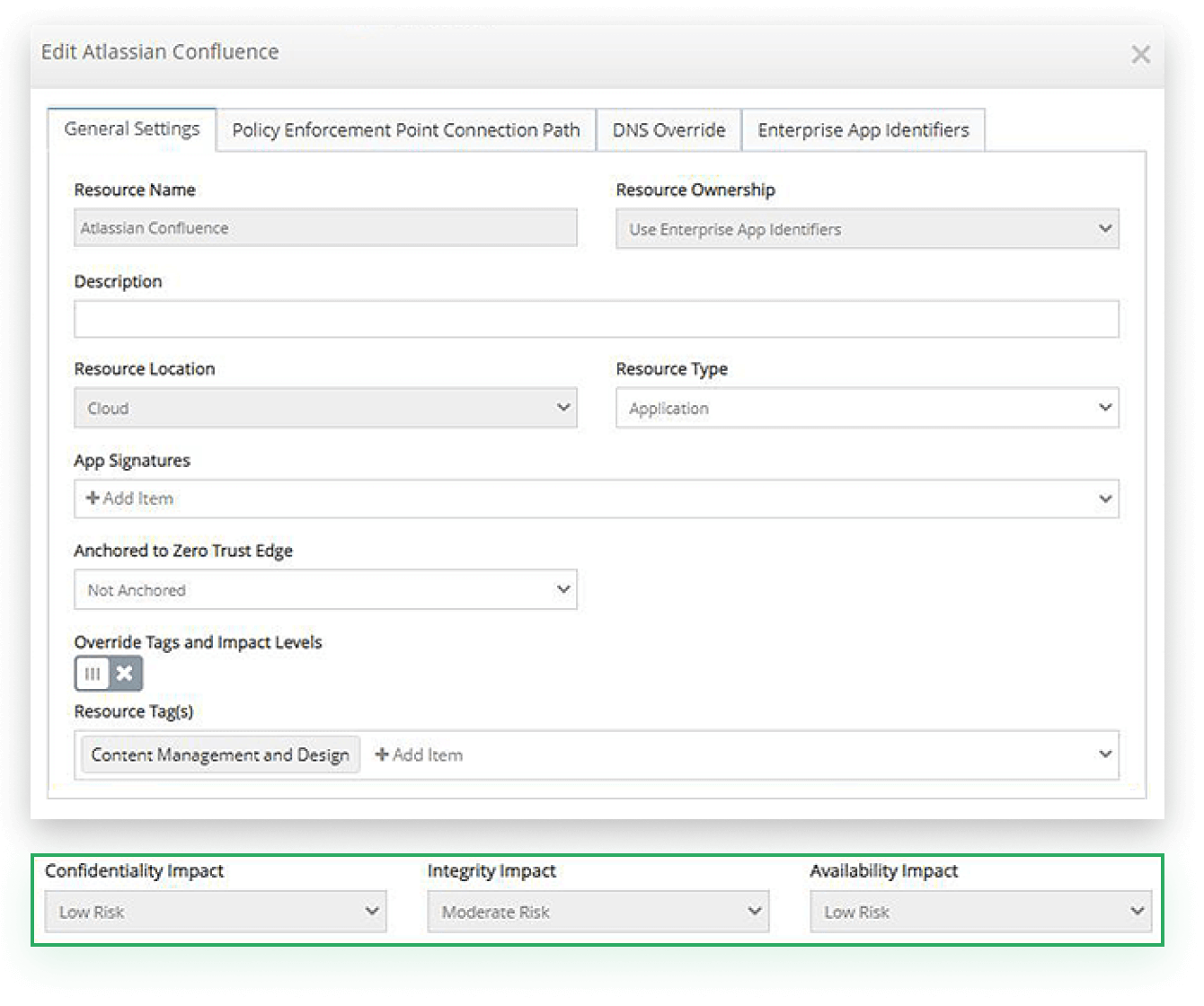
Each resource tag is associated with three security objectives, each with an impact level of low, moderate or high. The three security objectives match the definitions provided in NIST FIPS 199.
The three security objectives are:
- Confidentiality – Relates to unauthorized disclosure or data loss
- Integrity – Relates to the destruction of data or services
- Availability – Relates to the impact of interruption to a service or access to data
For each security objective, an impact level is assigned either a low, moderate or high rating, depending on the impact to the organization if that security objective was affected. By labeling resources, security objectives and impact levels are automatically assigned which provides a clear understanding of the landscape that needs to be protected.
Built-in catalog of pre-labeled resources, including type, security objectives and impact levels
The iboss Zero Trust Secure Access Service Edge has thousands of applications and services that are pre-classified by type, security objective and impact level. This allows resources to be automatically labeled and classified while reducing the time and effort to do so. The resources can be extracted from Azure AD or Okta and automatically labeled so that they are organized into a central resource database within the iboss platform.



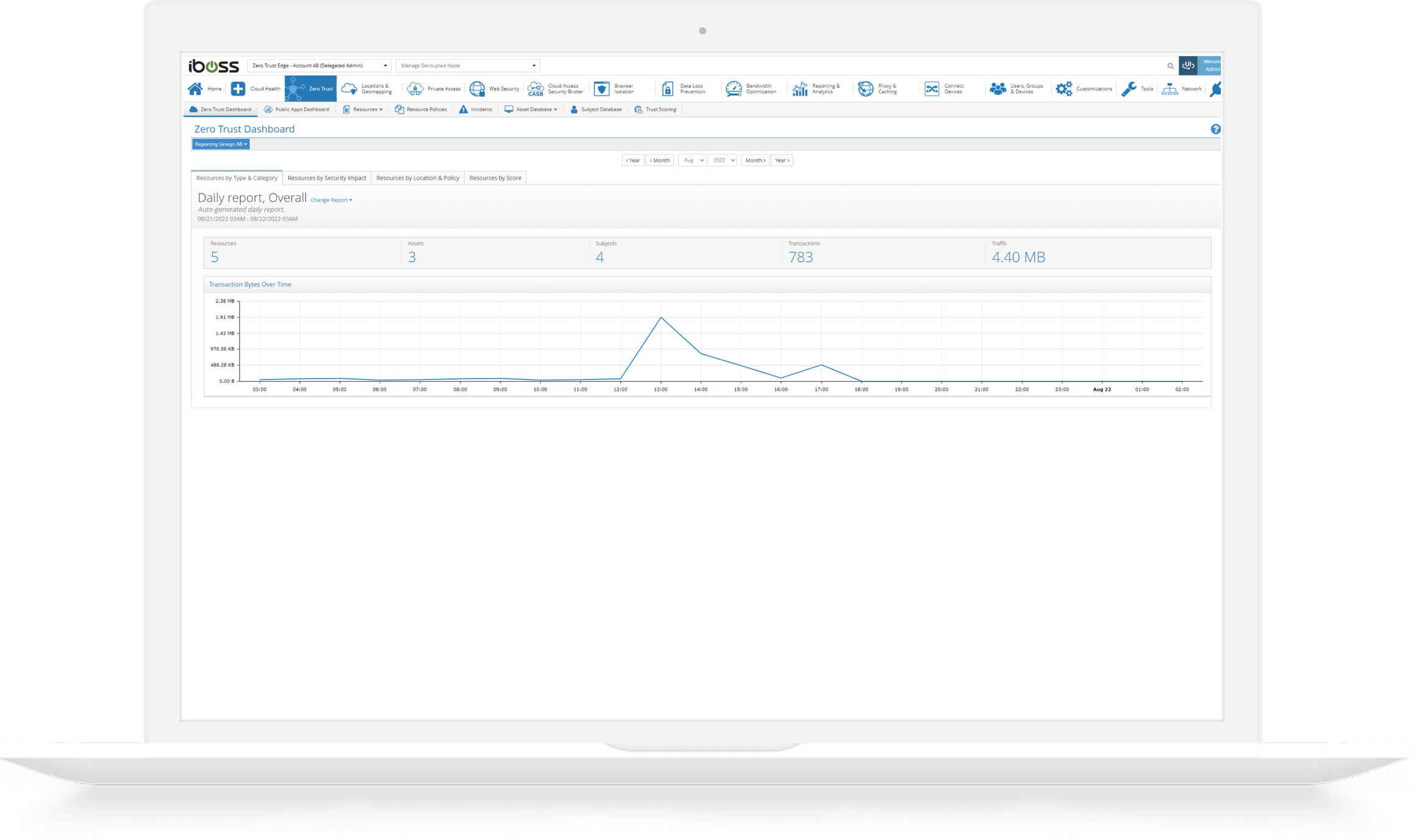
Reporting dashboards display labeled resources organized by type and security objective
Once resources are labeled, the iboss Zero Trust Secure Access Service Edge automatically creates the reports that present resources by type, category, security objective and impact level. The reporting dashboards can be filtered to show how resources interact with users and assets.
Additionally, the reporting dashboards show the number of accesses and risk scores for the resource. This information is made possible by leveraging the labels whenever users and assets interact with protected resources.