Having the right level of confidence for the identity of the user is critical as they interact with protected resources. The iboss Zero Trust Secure Access Service Edge can automatically require a higher level of authentication depending on the resource being accessed. This reduces the risk of an unauthorized user gaining access to critical applications, services and data.
Automatically step up authentication depending on resource being accessed
Automatically step up authentication depending on resource being accessed
The iboss Zero Trust Secure Access Service Edge can dynamically determine authentication level requirements depending on the application or service being accessed. When the right level of authentication is not met, the iboss platform will automatically redirect the user to the integrated Federated Identity Provider for authentication. Once the user authenticates successfully, access policies are checked and the user is automatically granted access to the resource originally requested.
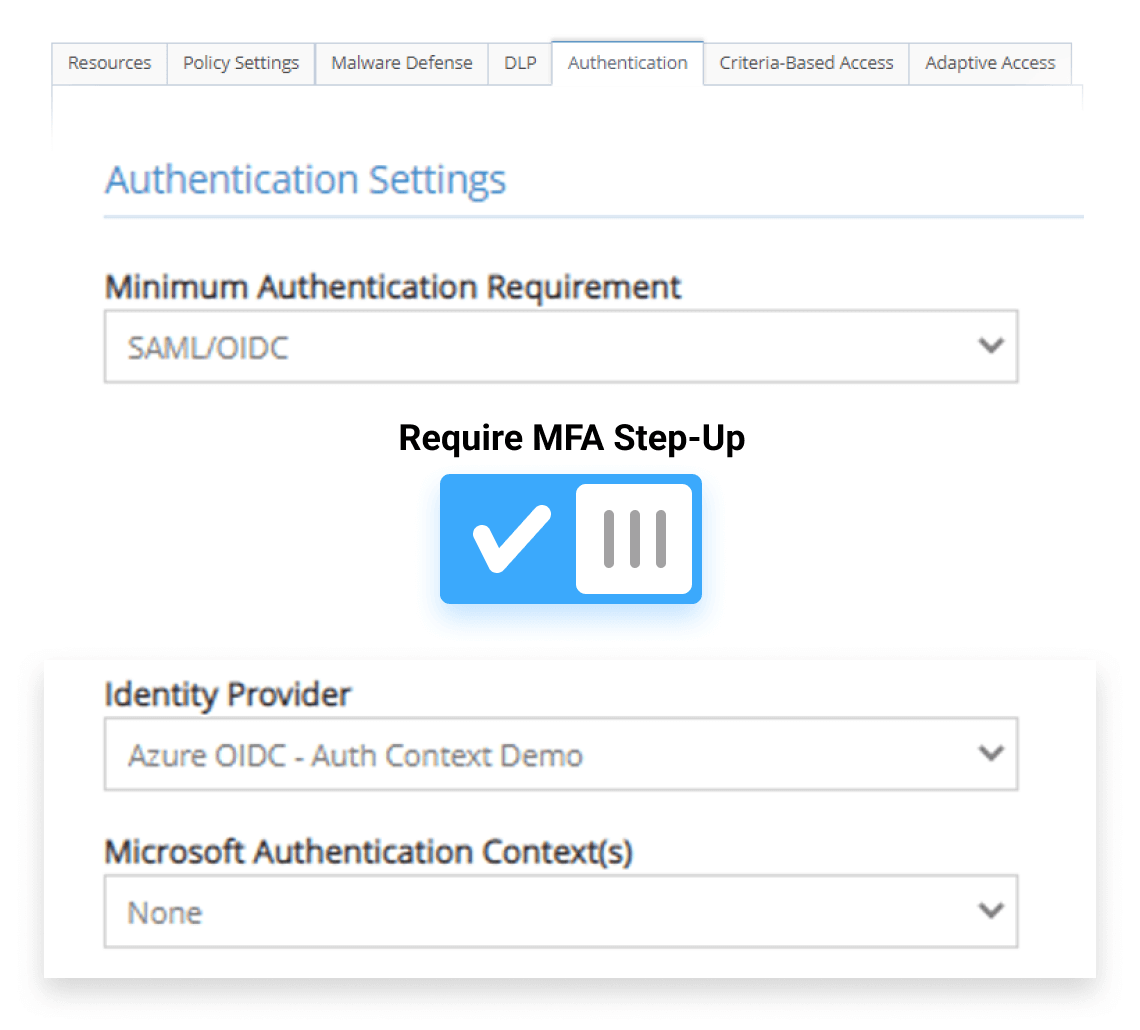
Force Multi-Factor Authentication when highly sensitive resources require it


Force Multi-Factor Authentication when highly sensitive resources require it
Depending on the resource type, multi-factor authentication may be required to ensure identity hijacking has not occurred. The iboss Zero Trust Secure Access Service Edge allows policies to be created for a resource or a group of resources that require multi-factor authentication. When a resource in the list is accessed and the user has not authenticated using MFA, the iboss platform will automatically redirect the user to authenticate via MFA before gaining access to the application or service.
Adaptive access capabilities can force step up authentication when access location is risky
The iboss Zero Trust Secure Access Service Edge allows policies to be linked based on identity and other context such as location. If a user is authenticating from a high risk location, policies can be created to force a higher level confidence authentication, such as MFA. The user is automatically redirected for authentication with the MFA requirement before gaining access to the resource from the high risk location.





